Category Archives: Security Tips
A USB dongle can hijack all your Web accounts and router in 30 seconds, even if your computer is locked
A security researcher finds a gaping hole in automatic network connections made by plugging in a dongle.
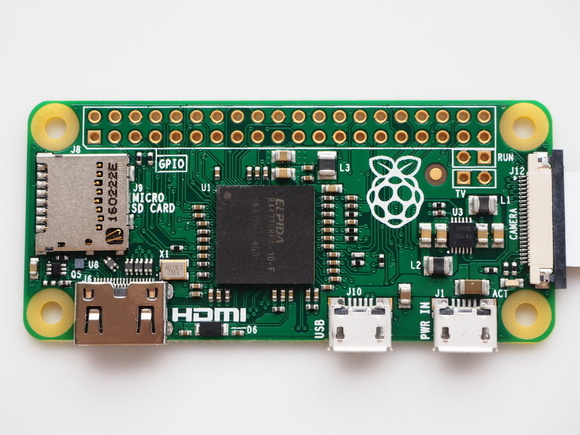
PoisonTap is built for the $5 Raspberry Pi Zero.
A proof of concept from security researcher and software developer Samy Kamkar shows that macOS, Windows, and Linux computers can have any previously active Web logins hijacked merely by plugging in a tiny Unix device via USB or Thunderbolt, even if the computer is locked and password protected, and possibly even when it seems to be asleep. It can also hijack many router brands on the same network.
How companies can deal with insider data theft
The recent arrest of a former NSA contractor is just the latest high-profile example.

Security firms are offering ways to protect companies from insider threats. Credit: IDGNS
To learn that your company’s confidential data was stolen, not by any hacker, but by an employee, is a nightmare scenario that no one wants to face.
But it’s also a risk that’s very real. The recent arrest of a former NSA contractor suspected of stealing classified government files is just the latest high profile example. And security experts say all companies need to be on guard against potential insider threats.
Restore a Windows 7 backup in Windows 10
It’s good to have a backup when you’ve lost your PC. But only if you can recover the files.

Aren’t you glad you have a backup? Without it, you would lose everything—instead of just the hardware.
I’m going to assume here that you used Windows 7’s built-in backup system, because that’s the default and the one you want for recovering data. (An image backup is for recovering Windows itself, which you don’t want to do on a new PC.) I’ll also assume that your new PC runs Windows 10.
These are the worst domains for harboring malware
For some new gTLDs the ratio of malicious domains is almost 80 percent, Spamhaus says.

5 things you need to know about ransomware, the scary malware that locks away data
Here are some tips to help protect your sensitive data









